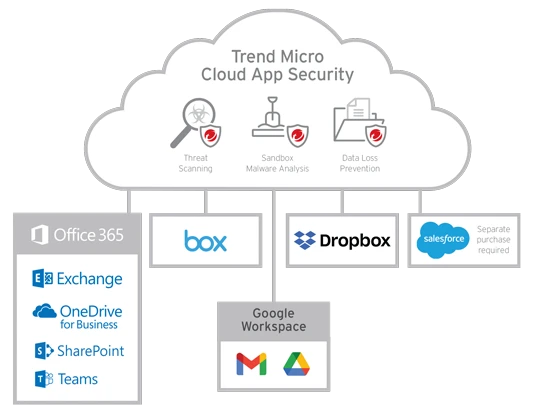
Uncovers ransomware, business email compromise (BEC), and other malicious attacks. </b>Cloud App Security finds unknown malware by using pre-execution machine learning. The document exploit detection engine discovers malware hidden in office files. Artificial intelligence checks email behavior, intention, and authorship to identify BEC attacks
In 2020, Cloud App Security caught 16.7 million high-risk threats that weren’t caught by Microsoft® Office 365® or Google Workspace™. This second layer of defense blocked threats beyond those detected by the cloud email services’ built-in security