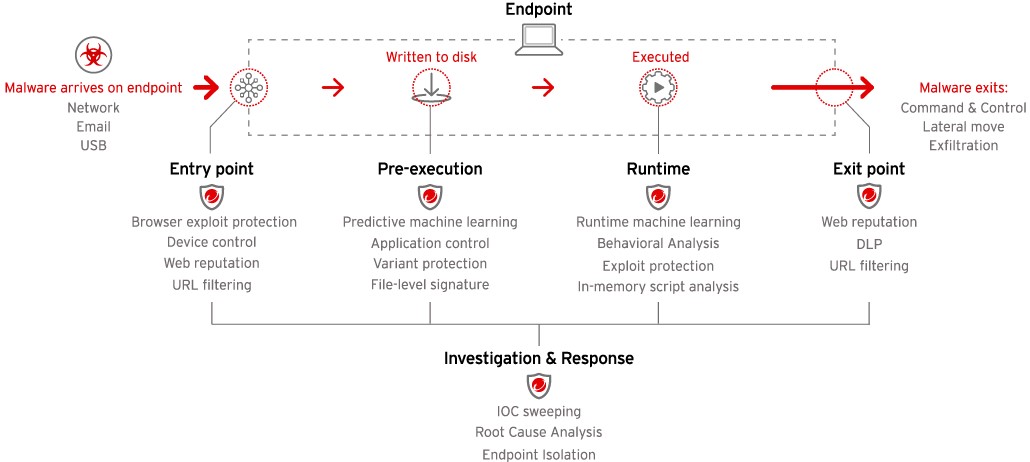
Trend Micro Apex One™ protection offers advanced automated threat detection and response against an ever-growing variety of threats, including fileless and ransomware. Our cross-generational blend of modern techniques provides highly tuned endpoint protection that maximizes performance and effectiveness.
TREND MICRO - APEX ONE
Endpoint Security
TREND MICRO - APEX ONE
Endpoint Security
Automated, insightful, all-in-one protection
Automated
Insightful
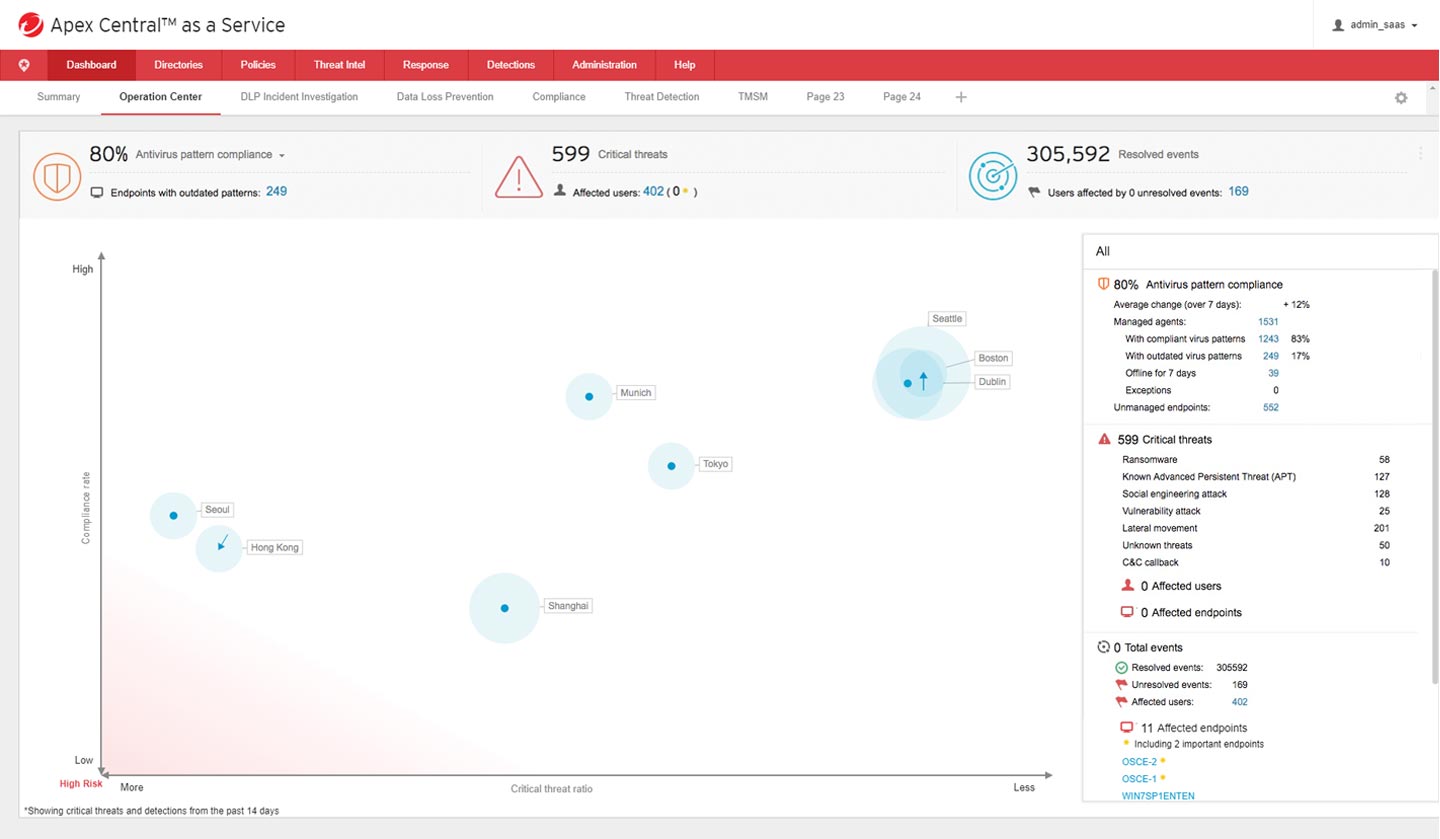
Get actionable insights, expanded investigative capabilities, and centralized visibility by using an advanced EDR toolset, strong SIEM integration, and an open API set. You have the option to perform correlated, extended threat investigations that go beyond the endpoint and augment your security teams with a managed detection and response service.
All-in-one
In an evolving technological landscape, you need security that goes beyond traditional antivirus. Apex One offers threat detection, response, and investigation within a single agent. Eliminate multiple vendors and consoles and gain deployment flexibility through both SaaS and on-premises deployment options.
Advanced detection techniques
Apex One leverages a blend of cross-generational threat techniques to provide the broadest protection against all types of threats, giving you:

Pre-execution and runtime machine learning

More accurate detection of advanced malware, such as fileless, living off the land, and ransomware threats


Ultimate protection against vulnerabilities
More than just a scan, Apex One Vulnerability Protection uses a host-based intrusion prevention system (HIPS) to virtually patch known and unknown vulnerabilities before a patch is available or deployable:

- Eliminating risk exposure by shielding vulnerabilities through innovative virtual patching capabilities and world-class research
- Extending protection to critical platforms and physical or virtual devices
- Reducing recovery and emergency patching downtime
- Identifying vulnerabilities based on CVE, MS-ID, and severity
- Detecting more vulnerabilities than any other vendor by leveraging our industry-leading vulnerability research
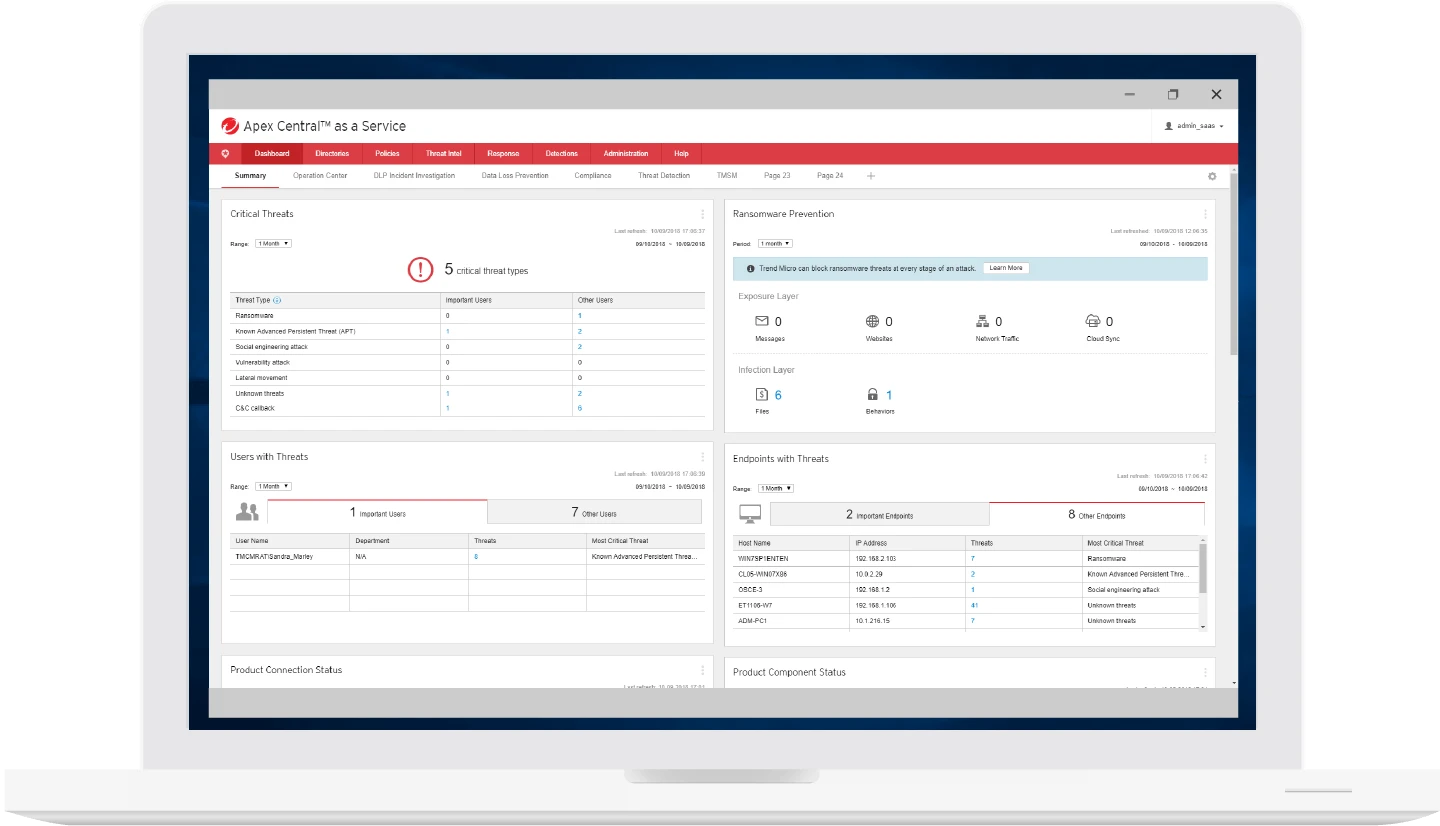
Integrated detection and response
Leverage advanced detection techniques to proactively detect and respond to threats before any damage can be done. With Trend Micro Vision One™, you gain full-featured XDR capabilities to deepen detection, investigation, and response capabilities, so you can extend them across multiple security layers for broad visibility and response to threats impacting the entire organization.
Learn how you can improve your email and endpoint security with XDR. Experience Trend Micro Vision One™ for free within a virtual pre-configured lab.
- Hunt for indicators of attack (IoA) and define the attacker’s intent in real time
- Sweep user timelines (telemetry) for indicators of compromise (IoCs) to determine the impact of targeted attacks
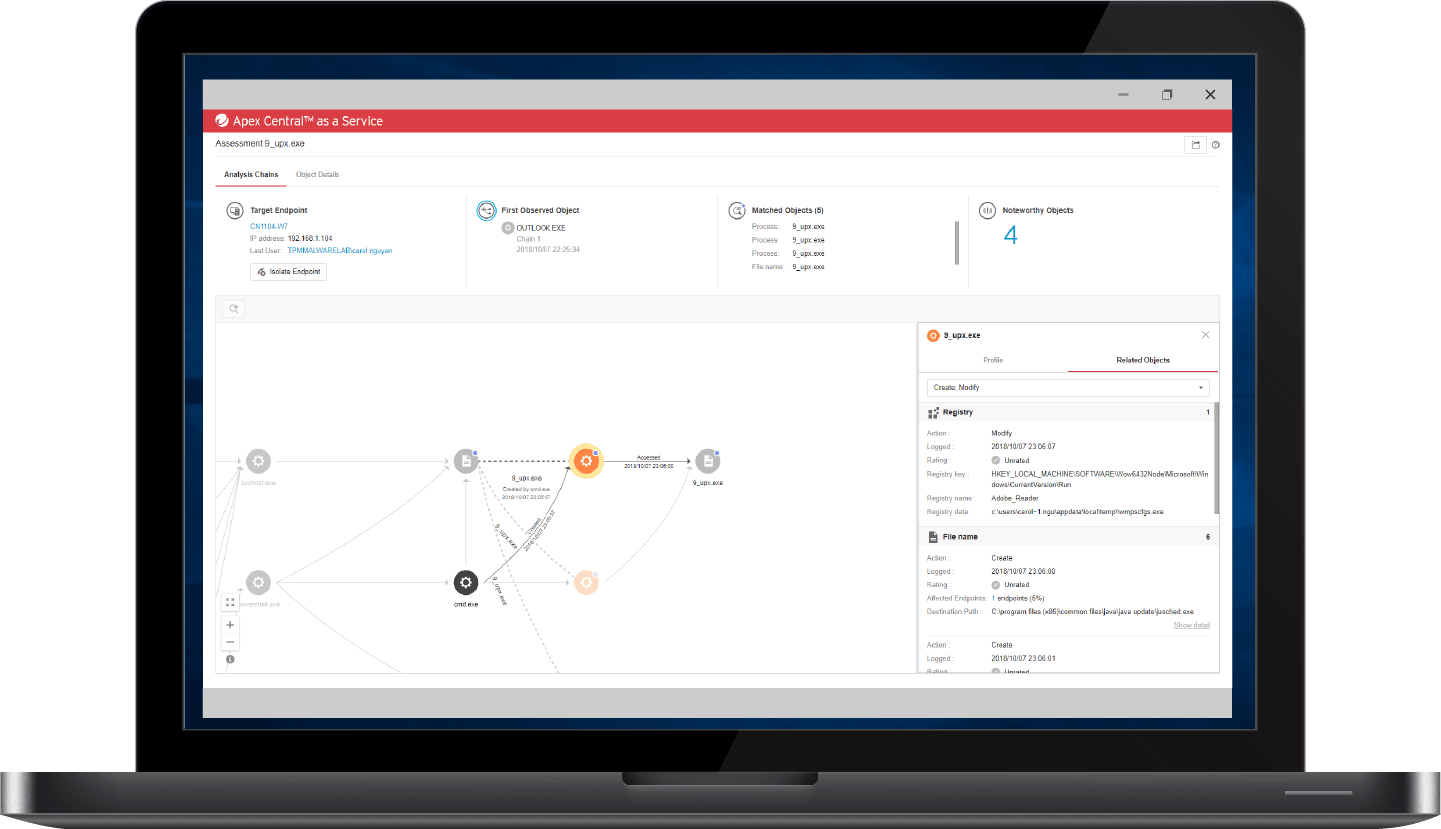
- Employ an interactive root cause analysis diagram to drill down on a detection, and respond by isolating or terminating processes and updating protection points
- Have the option to go beyond a single vector approach by correlating events across email, endpoints, servers, cloud workloads, and networks


Hunt for indicators of attack (IoA) and define the attacker’s intent in real time

Sweep user timelines (telemetry) for indicators of compromise (IoCs) to determine the impact of targeted attacks
Employ an interactive root cause analysis diagram to drill down on a detection, and respond by isolating or terminating processes and updating protection points

Have the option to go beyond a single vector approach by correlating events across email, endpoints, servers, cloud workloads, and networks
Effective security for your sensitive data
Protect your sensitive data, on or off network, for maximum visibility and control. Endpoint encryption,* integrated DLP, and device control:
- Cover the broadest range of devices, applications, and file types
- Assist with most regulatory compliance, including GDPR
- Protect data with full-disk, folder, file, and removable media encryption
- Set granular policies for device control and data management
- Manage Microsoft® BitLocker®, and Apple® FileVault® encryption keys


Enhanced application control against malicious software
Prevent unknown and unwanted applications from executing on your corporate endpoints. Trend Micro Apex One™ Application Control allows you to:
- Block malicious software from running using customizable lockdown, safelisting, and denylisting policies
- Create dynamic policies by leveraging Trend Micro’s application categorization and reputation intelligence to reduce management overhead
- Correlate data from millions of application events to identify threats and maintain an up-to-date database of validated applications

TrendConnect lets users stay current with real-time product alerts and threat information
With the TrendConnect app customers will be able to:
- Instantly see deployment status to avoid running out-of-date versions of Trend Micro Apex One
- Align deployments with Trend Micro Apex One best practices to ensure your endpoints are optimally protected
- Stay one step ahead with real-time advisories of new vulnerabilities/threats and notifications of new essential and critical patches

Centralized visibility and control
Enable consistent security management, visibility, and reporting across multiple layers of interconnected security through a centralized console.



How it works